tutorials, tips, tricks, commands, programming, linux, windows, database, sql, python, programming language, Fedora, drawing, painting, tutorial, tutorials
Monday, July 3, 2017
News: Linux kernel 4.12 released .
On 2 July, Linus Torvalds released the kernel 4.12, and it is available for download on kernel.org.
Linux 4.12 provides support for USB Type C in the form of a port management - that provides the correct power consumption.
Some significant changes are once again from the AMD-GPU driver.
About Data Integrity Protection, the device mapper driver receives an extension called dm_integrity to check the integrity of encrypted data on block devices and to protect it in the long term.
Read more about this news here.
Wednesday, June 7, 2017
DB Browser - tool for databases.
Also is a good tool for learning and test database queries.
About this tool the development team tells us:
DB Browser for SQLite is a high quality, visual, open-source tool to create, design, and edit database files compatible with SQLite. It is for users and developers wanting to create databases, search, and edit data. It uses a familiar spreadsheet-like interface, and you don't need to learn complicated SQL commands.
To install it just use this:
About this tool the development team tells us:
DB Browser for SQLite is a high quality, visual, open-source tool to create, design, and edit database files compatible with SQLite. It is for users and developers wanting to create databases, search, and edit data. It uses a familiar spreadsheet-like interface, and you don't need to learn complicated SQL commands.
- Controls and wizards are available for users to:
- Create and compact database files
- Create, define, modify and delete tables
- Create, define and delete indexes
- Browse, edit, add and delete records Search records
- Import and export records as text
- Import and export tables from/to CSV files Import and export databases from/to SQL dump files
- Issue SQL queries and inspect the results
- Examine a log of all SQL commands issued by the application
To install it just use this:
$ sudo dnf install sqlitebrowser
Posted by
Cătălin George Feștilă
 Labels:
2017,
2017 news,
crossplatform,
Fedora,
Fedora 25,
linux tools,
tool,
tutorial,
tutorials,
windows
Labels:
2017,
2017 news,
crossplatform,
Fedora,
Fedora 25,
linux tools,
tool,
tutorial,
tutorials,
windows
Wednesday, May 24, 2017
Best password management tool.
This suite of tools come with many features free and one good premium option.
The Password Tote tools provides secure password management through software and services on multiple platforms and work very well with software downloads for Windows, Mac OS X, Safari, Chrome, Firefox, iOS (iPhone, iPod Touch, iPad), Android.
You can download this from downloads page.
Synchronization between browser extensions and utilities is fast and does not confuse the user in navigation. Importing files is fast for the csv file dedicated to dozens of passwords.
A very good aspect was the compromise solution for custom import with a generic csv file.
The utility generates this file and you can fill it with the necessary login data for your web sites.
The other csv import options did not work for me, I guess the problems are incompatible with the other files exported by the dedicated software.
I used it with YubiKey and it worked very well. It's the only utility that allowed me to connect with YubiKey, the other utilities demand a premium version.
How to enable YubiKeys and password tote.
The Password Tote tools provides secure password management through software and services on multiple platforms and work very well with software downloads for Windows, Mac OS X, Safari, Chrome, Firefox, iOS (iPhone, iPod Touch, iPad), Android.
You can download this from downloads page.
| Features Outline | Free | Premium |
| Website Access | ● | |
| Browser Extensions | ● | |
| Desktop Software | ● | |
| Mobile Software | ● | |
| Password Sharing | ● | |
| YubiKey Support | ● | |
| Price | Free | $2.99 a month or 2 Years at a 16% savings |
| Description | This will allow you to use the website version completely free. It also gives you access to fill your passwords from the browser extensions. It does not provide access to the desktop software or mobile phone software. | Premium gives you access to your passwords from all versions of Password Tote, including the desktop software and mobile phone versions. |
Synchronization between browser extensions and utilities is fast and does not confuse the user in navigation. Importing files is fast for the csv file dedicated to dozens of passwords.
A very good aspect was the compromise solution for custom import with a generic csv file.
The utility generates this file and you can fill it with the necessary login data for your web sites.
The other csv import options did not work for me, I guess the problems are incompatible with the other files exported by the dedicated software.
I used it with YubiKey and it worked very well. It's the only utility that allowed me to connect with YubiKey, the other utilities demand a premium version.
How to enable YubiKeys and password tote.
- First log in to your Password Tote account.
- Click Account, then Manage YubiKeys. You will arrive at the YubiKey Management page.
- Click Add YubiKey to register your YubiKey with your Password Tote account.
- Fill in the required details. If successful, your YubiKey will be displayed in the list as shown in the screen shot below.
Posted by
Cătălin George Feștilă
 Labels:
2017,
Fedora,
hardware,
linux,
linux tools,
passwords,
tool,
windows,
YubiKeys
Labels:
2017,
Fedora,
hardware,
linux,
linux tools,
passwords,
tool,
windows,
YubiKeys
Tuesday, May 23, 2017
The tool Noodl for design and web development.
This tool will help you understand something about data structuring, node building, web development and design.
This application comes with interactive lessons and documentation.
Note: I tested some lessons and are not very easy. Thus, some links between the nodes do not appear with all the labels, unless they are made inversely, in this case on the work surface the links are no longer one-way (with the arrow arrow) but only punctually between the nodes.
It can be downloaded here for the following operating systems :
This application comes with interactive lessons and documentation.
Note: I tested some lessons and are not very easy. Thus, some links between the nodes do not appear with all the labels, unless they are made inversely, in this case on the work surface the links are no longer one-way (with the arrow arrow) but only punctually between the nodes.
It can be downloaded here for the following operating systems :
- Version 1.2.3 (MacOS)
- Version 1.2.3 (Win x64 Installer)
- Version 1.2.3 (Linux x86 64)
Posted by
Cătălin George Feștilă
 Labels:
2017,
design,
linux,
linux tools,
mac,
tool,
web development,
windows
Labels:
2017,
design,
linux,
linux tools,
mac,
tool,
web development,
windows
Sunday, May 7, 2017
The JetBrains I.D.E. software .
I tested the JetBrains Rider, the emerging .NET I.D.E. from JetBrains in the past.
Is good and this is new into the I.D.E. area of development.
What is this software?
The JetBrains Rider is a new .NET I.D.E. based on the IntelliJ platform and ReSharper.
First I take a look into my Fedora distro to see it is something about JetBrains:
This software come with a good wizard interface.
The application has many ways to deal with your source code and settings for any user. The colors of this software are ergonomic for users. They are:
Is good and this is new into the I.D.E. area of development.
What is this software?
The JetBrains Rider is a new .NET I.D.E. based on the IntelliJ platform and ReSharper.
First I take a look into my Fedora distro to see it is something about JetBrains:
[root@localhost mythcat]# dnf search jetbrains
Last metadata expiration check: 1:19:59 ago on Tue Feb 21 12:42:57 2017.
============================ N/S Matched: jetbrains ============================
jetbrains-annotations-javadoc.noarch : Javadoc for jetbrains-annotations
jetbrains-annotations.noarch : IntelliJ IDEA Annotations[mythcat@localhost ~]$ cd Rider-171.3085.362/bin/
[mythcat@localhost bin]$ ll
total 7120
-rw-r--r--. 1 mythcat mythcat 2568 Feb 15 23:02 backend-log.xml
-rwxr-xr-x. 1 mythcat mythcat 217 Feb 15 23:02 format.sh
-rwxr-xr-x. 1 mythcat mythcat 23072 Feb 15 23:02 fsnotifier
-rwxr-xr-x. 1 mythcat mythcat 29648 Feb 15 23:02 fsnotifier64
-rwxr-xr-x. 1 mythcat mythcat 26453 Feb 15 23:02 fsnotifier-arm
-rw-r--r--. 1 mythcat mythcat 10491 Feb 15 23:02 idea.properties
-rwxr-xr-x. 1 mythcat mythcat 268 Feb 15 23:02 inspect.sh
-rw-r--r--. 1 mythcat mythcat 3449944 Feb 15 23:02 libyjpagent-linux64.so
-rw-r--r--. 1 mythcat mythcat 3679036 Feb 15 23:02 libyjpagent-linux.so
-rw-r--r--. 1 mythcat mythcat 4138 Feb 15 23:02 log.xml
-rwxr-xr-x. 1 mythcat mythcat 410 Feb 15 23:02 printenv.py
-rwxr-xr-x. 1 mythcat mythcat 590 Feb 15 23:02 restart.py
-rw-r--r--. 1 mythcat mythcat 359 Feb 15 23:02 rider64.vmoptions
-rw-r--r--. 1 mythcat mythcat 9222 Feb 15 23:02 rider.png
-rwxr-xr-x. 1 mythcat mythcat 6619 Feb 15 23:02 rider.sh
-rw-r--r--. 1 mythcat mythcat 367 Feb 15 23:02 rider.vmoptions[mythcat@localhost bin]$ ./rider.sh
[YourKit Java Profiler 2016.02-b43] Log file: /home/mythcat/.yjp/log/Rider10-17590.log
Feb 21, 2017 2:05:43 PM java.util.prefs.FileSystemPreferences$6 run
WARNING: Prefs file removed in background /home/mythcat/.java/.userPrefs/prefs.xml
Installation home directory: /home/mythcat/Rider-171.3085.362
System directory: /home/mythcat/.Rider10/system
Config directory: /home/mythcat/.Rider10/config
Log directory: /home/mythcat/.Rider10/system/log
Full cold solution load with caches took 22053 milliseconds.This software come with a good wizard interface.
The application has many ways to deal with your source code and settings for any user. The colors of this software are ergonomic for users. They are:
- Memory: 4 GB or higher
- Operating system:
- Windows 10, 8.1, 8 or 7. 64-bit distributions only.
- OS X 10.10+. 64-bit distributions only.
- Linux. 64-bit distributions only.
Posted by
Cătălin George Feștilă
 Labels:
2017,
Fedora,
Fedora 25,
IDE,
linux,
linux tools,
programming,
software
Labels:
2017,
Fedora,
Fedora 25,
IDE,
linux,
linux tools,
programming,
software
Thursday, April 20, 2017
Fedora 25 and fix python modules.
This tutorial is a simple way to fix your python modules under Fedora distro.
I used Fedora 25 and python 2.7.13 version.
First try to use this command:
Another example is this lib: opensslv.h
So install this:
I used Fedora 25 and python 2.7.13 version.
First try to use this command:
pip freeze --local | grep -v '^\-e' | cut -d = -f 1 | xargs -n1 pip install -U- to skip "-e" package definitions;
- the newer versions of pip allow you to list outdated python modules;
- added -n1 to xargs, prevents stopping everything if updating one python module fails;
...fatal error: Python.h...[root@localhost mythcat]# dnf install python-devel.x86_64 python-devel.i686Another example is this lib: opensslv.h
So install this:
[root@localhost mythcat]# dnf install openssl-devel.x86_64
Last metadata expiration check: 1:58:33 ago on Thu Apr 20 18:52:10 2017.
Dependencies resolved.
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
openssl-devel x86_64 1:1.0.2k-1.fc25 updates 1.5 M
Transaction Summary
================================================================================
Install 1 Package
Total download size: 1.5 M
Installed size: 3.1 M
Is this ok [y/N]: y
Downloading Packages:
openssl-devel-1.0.2k-1.fc25.x86_64.rpm 580 kB/s | 1.5 MB 00:02
--------------------------------------------------------------------------------
Total 394 kB/s | 1.5 MB 00:03
Running transaction check
Transaction check succeeded.
Running transaction test
Transaction test succeeded.
Running transaction
Installing : openssl-devel-1:1.0.2k-1.fc25.x86_64 1/1
Verifying : openssl-devel-1:1.0.2k-1.fc25.x86_64 1/1
Installed:
openssl-devel.x86_64 1:1.0.2k-1.fc25
Complete!pip freeze --local | grep -v '^\-e' | cut -d = -f 1 | xargs -n1 pip install -U[root@localhost mythcat]# pip list --outdated --format=freeze
CCColUtils==1.4
cryptography==1.5.3
evdev==0.6.1
fedmsg==0.18.2
ipykernel==4.5.2
M2Crypto==0.25.1
matplotlib==1.5.2rc2
mercurial==3.8.1
mysqlclient==1.3.7
psutil==4.3.0
pycryptopp==0.6.0.1206569328141510525648634803928199668821045408958
pyopencl==2015.2
pyOpenSSL==16.0.0
pyxattr==0.5.3
requests-kerberos==0.10.0
service-identity==14.0.0
Sphinx==1.5.3
SQLAlchemy==1.1.6
Tempita==0.5.1
tornado==4.4.2
Twisted==16.3.0
txZMQ==0.7.4
[root@localhost mythcat]# pip list --outdated --format=freeze
mysqlclient==1.3.7
pyopencl==2015.2
pyxattr==0.5.3
Posted by
Cătălin George Feștilă
 Labels:
2017,
Fedora,
Fedora 25,
linux tools,
python,
python modules,
script,
tutorial,
tutorials
Labels:
2017,
Fedora,
Fedora 25,
linux tools,
python,
python modules,
script,
tutorial,
tutorials
Tuesday, April 18, 2017
The GUI for Clam antivirus - clamtk .
Today I will show you how to use a GUI for clam antivirus named clamtk.
The ClamTk is a graphical front-end for ClamAV using Perl and Gtk libraries.
The first step when opening ClamTK GUI is to select "Update Assistant".
You can choose "I would like to update signatures myself".
You should go back to the home screen of ClamTK and click "Settings"
Also, you can use this GUI to scan, update and analysis your operating system.
The ClamTk is a graphical front-end for ClamAV using Perl and Gtk libraries.

[root@localhost mythcat]# dnf search clamtk
Last metadata expiration check: 1:24:49 ago on Tue Apr 18 17:01:00 2017.
============================= N/S Matched: clamtk ==============================
clamtk.noarch : Easy to use graphical user interface for Clam anti virus[root@localhost mythcat]# dnf install clamtk.noarch
Last metadata expiration check: 1:31:00 ago on Tue Apr 18 17:01:00 2017.
Dependencies resolved.
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
clamtk noarch 5.24-1.fc25 updates 218 k
perl-Cairo x86_64 1.106-3.fc25 fedora 125 k
perl-File-Listing noarch 6.04-13.fc25 fedora 17 k
perl-Glib x86_64 1.321-2.fc25 fedora 364 k
perl-Gtk2 x86_64 1.2498-3.fc25 fedora 1.8 M
perl-HTTP-Cookies noarch 6.01-13.fc25 fedora 29 k
perl-HTTP-Negotiate noarch 6.01-13.fc25 fedora 21 k
perl-JSON noarch 2.90-7.fc25 fedora 98 k
perl-LWP-Protocol-https noarch 6.07-1.fc25 updates 16 k
perl-Locale-gettext x86_64 1.07-4.fc25 fedora 26 k
perl-NTLM noarch 1.09-13.fc25 fedora 23 k
perl-Net-HTTP noarch 6.13-1.fc25 updates 41 k
perl-Pango x86_64 1.227-3.fc25 fedora 190 k
perl-Test-Simple noarch 1.302062-1.fc25 fedora 410 k
perl-Text-CSV noarch 1.91-4.fc25 updates 103 k
perl-Time-Piece x86_64 1.31-385.fc25 updates 88 k
perl-WWW-RobotRules noarch 6.02-14.fc25 fedora 22 k
perl-libwww-perl noarch 6.15-3.fc25 fedora 208 k
Transaction Summary
================================================================================
Install 18 Packages
Total download size: 3.7 M
Installed size: 10 M
Is this ok [y/N]: y
Downloading Packages:
(1/18): clamtk-5.24-1.fc25.noarch.rpm 517 kB/s | 218 kB 00:00
(2/18): perl-Glib-1.321-2.fc25.x86_64.rpm 662 kB/s | 364 kB 00:00
(3/18): perl-Locale-gettext-1.07-4.fc25.x86_64. 296 kB/s | 26 kB 00:00
(4/18): perl-Gtk2-1.2498-3.fc25.x86_64.rpm 2.3 MB/s | 1.8 MB 00:00
(5/18): perl-libwww-perl-6.15-3.fc25.noarch.rpm 1.4 MB/s | 208 kB 00:00
(6/18): perl-JSON-2.90-7.fc25.noarch.rpm 181 kB/s | 98 kB 00:00
(7/18): perl-Cairo-1.106-3.fc25.x86_64.rpm 439 kB/s | 125 kB 00:00
(8/18): perl-Pango-1.227-3.fc25.x86_64.rpm 1.7 MB/s | 190 kB 00:00
(9/18): perl-File-Listing-6.04-13.fc25.noarch.r 204 kB/s | 17 kB 00:00
(10/18): perl-HTTP-Cookies-6.01-13.fc25.noarch. 375 kB/s | 29 kB 00:00
(11/18): perl-HTTP-Negotiate-6.01-13.fc25.noarc 250 kB/s | 21 kB 00:00
(12/18): perl-Test-Simple-1.302062-1.fc25.noarc 1.5 MB/s | 410 kB 00:00
(13/18): perl-NTLM-1.09-13.fc25.noarch.rpm 160 kB/s | 23 kB 00:00
(14/18): perl-WWW-RobotRules-6.02-14.fc25.noarc 168 kB/s | 22 kB 00:00
(15/18): perl-Net-HTTP-6.13-1.fc25.noarch.rpm 315 kB/s | 41 kB 00:00
(16/18): perl-Time-Piece-1.31-385.fc25.x86_64.r 638 kB/s | 88 kB 00:00
(17/18): perl-LWP-Protocol-https-6.07-1.fc25.no 77 kB/s | 16 kB 00:00
(18/18): perl-Text-CSV-1.91-4.fc25.noarch.rpm 297 kB/s | 103 kB 00:00
--------------------------------------------------------------------------------
Total 1.3 MB/s | 3.7 MB 00:02
Running transaction check
Transaction check succeeded.
Running transaction test
Transaction test succeeded.
Running transaction
Installing : perl-Glib-1.321-2.fc25.x86_64 1/18
Installing : perl-Net-HTTP-6.13-1.fc25.noarch 2/18
Installing : perl-Cairo-1.106-3.fc25.x86_64 3/18
Installing : perl-Pango-1.227-3.fc25.x86_64 4/18
Installing : perl-Time-Piece-1.31-385.fc25.x86_64 5/18
Installing : perl-Text-CSV-1.91-4.fc25.noarch 6/18
Installing : perl-WWW-RobotRules-6.02-14.fc25.noarch 7/18
Installing : perl-NTLM-1.09-13.fc25.noarch 8/18
Installing : perl-HTTP-Negotiate-6.01-13.fc25.noarch 9/18
Installing : perl-HTTP-Cookies-6.01-13.fc25.noarch 10/18
Installing : perl-File-Listing-6.04-13.fc25.noarch 11/18
Installing : perl-libwww-perl-6.15-3.fc25.noarch 12/18
Installing : perl-LWP-Protocol-https-6.07-1.fc25.noarch 13/18
Installing : perl-Test-Simple-1.302062-1.fc25.noarch 14/18
Installing : perl-Gtk2-1.2498-3.fc25.x86_64 15/18
Installing : perl-Locale-gettext-1.07-4.fc25.x86_64 16/18
Installing : perl-JSON-2.90-7.fc25.noarch 17/18
Installing : clamtk-5.24-1.fc25.noarch 18/18
Verifying : clamtk-5.24-1.fc25.noarch 1/18
Verifying : perl-Glib-1.321-2.fc25.x86_64 2/18
Verifying : perl-Gtk2-1.2498-3.fc25.x86_64 3/18
Verifying : perl-JSON-2.90-7.fc25.noarch 4/18
Verifying : perl-Locale-gettext-1.07-4.fc25.x86_64 5/18
Verifying : perl-libwww-perl-6.15-3.fc25.noarch 6/18
Verifying : perl-Cairo-1.106-3.fc25.x86_64 7/18
Verifying : perl-Pango-1.227-3.fc25.x86_64 8/18
Verifying : perl-Test-Simple-1.302062-1.fc25.noarch 9/18
Verifying : perl-File-Listing-6.04-13.fc25.noarch 10/18
Verifying : perl-HTTP-Cookies-6.01-13.fc25.noarch 11/18
Verifying : perl-HTTP-Negotiate-6.01-13.fc25.noarch 12/18
Verifying : perl-NTLM-1.09-13.fc25.noarch 13/18
Verifying : perl-WWW-RobotRules-6.02-14.fc25.noarch 14/18
Verifying : perl-Net-HTTP-6.13-1.fc25.noarch 15/18
Verifying : perl-LWP-Protocol-https-6.07-1.fc25.noarch 16/18
Verifying : perl-Text-CSV-1.91-4.fc25.noarch 17/18
Verifying : perl-Time-Piece-1.31-385.fc25.x86_64 18/18
Installed:
clamtk.noarch 5.24-1.fc25
perl-Cairo.x86_64 1.106-3.fc25
perl-File-Listing.noarch 6.04-13.fc25
perl-Glib.x86_64 1.321-2.fc25
perl-Gtk2.x86_64 1.2498-3.fc25
perl-HTTP-Cookies.noarch 6.01-13.fc25
perl-HTTP-Negotiate.noarch 6.01-13.fc25
perl-JSON.noarch 2.90-7.fc25
perl-LWP-Protocol-https.noarch 6.07-1.fc25
perl-Locale-gettext.x86_64 1.07-4.fc25
perl-NTLM.noarch 1.09-13.fc25
perl-Net-HTTP.noarch 6.13-1.fc25
perl-Pango.x86_64 1.227-3.fc25
perl-Test-Simple.noarch 1.302062-1.fc25
perl-Text-CSV.noarch 1.91-4.fc25
perl-Time-Piece.x86_64 1.31-385.fc25
perl-WWW-RobotRules.noarch 6.02-14.fc25
perl-libwww-perl.noarch 6.15-3.fc25
Complete!The first step when opening ClamTK GUI is to select "Update Assistant".
You can choose "I would like to update signatures myself".
You should go back to the home screen of ClamTK and click "Settings"
Also, you can use this GUI to scan, update and analysis your operating system.
Monday, April 17, 2017
Fedora 25 : The YARA tool for Linux security - part 001.
The YARA tool is a multi-platform program running on Windows, Linux and Mac OS X.
The YARA is designed to help malware researchers identify and classify malware samples.
It’s been called for security researchers and everyone else.
Yara provides an easy and effective way to write custom rules based on strings or byte sequences and allows you to make your own detection tools.
You can create descriptions of malware families based on textual or binary patterns or whatever you want to describe.
This descriptions or rules consists of a set of strings and a boolean expression which determine its logic.
The official website can be found here.
The First you need to install the yara tool under your Linux OS.
I used Fedora 25 distro.
The base of the syntax of a YARA rule set is this:
The YARA is designed to help malware researchers identify and classify malware samples.
It’s been called for security researchers and everyone else.
Yara provides an easy and effective way to write custom rules based on strings or byte sequences and allows you to make your own detection tools.
You can create descriptions of malware families based on textual or binary patterns or whatever you want to describe.
This descriptions or rules consists of a set of strings and a boolean expression which determine its logic.
The official website can be found here.
The First you need to install the yara tool under your Linux OS.
I used Fedora 25 distro.
[root@localhost mythcat]# dnf install yara
Last metadata expiration check: 0:49:37 ago on Sun Apr 16 22:23:14 2017.
Dependencies resolved.
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
yara x86_64 3.5.0-7.fc25 updates-testing 191 k
Transaction Summary
================================================================================
Install 1 Package
Total download size: 191 k
Installed size: 861 k
Is this ok [y/N]: y
Downloading Packages:
yara-3.5.0-7.fc25.x86_64.rpm 171 kB/s | 191 kB 00:01
--------------------------------------------------------------------------------
Total 92 kB/s | 191 kB 00:02
Running transaction check
Transaction check succeeded.
Running transaction test
Transaction test succeeded.
Running transaction
Installing : yara-3.5.0-7.fc25.x86_64 1/1
Verifying : yara-3.5.0-7.fc25.x86_64 1/1
Installed:
yara.x86_64 3.5.0-7.fc25
Complete![mythcat@localhost ~]$ yara
yara: wrong number of arguments
Usage: yara [OPTION]... RULES_FILE FILE | DIR | PID
Try `--help` for more options
[mythcat@localhost ~]$ yara --help
YARA 3.5.0, the pattern matching swiss army knife.
Usage: yara [OPTION]... RULES_FILE FILE | DIR | PID
Mandatory arguments to long options are mandatory for short options too.
-t, --tag=TAG print only rules tagged as TAG
-i, --identifier=IDENTIFIER print only rules named IDENTIFIER
-n, --negate print only not satisfied rules (negate)
-D, --print-module-data print module data
-g, --print-tags print tags
-m, --print-meta print metadata
-s, --print-strings print matching strings
-e, --print-namespace print rules' namespace
-p, --threads=NUMBER use the specified NUMBER of threads to scan a directory
-l, --max-rules=NUMBER abort scanning after matching a NUMBER of rules
-d VAR=VALUE define external variable
-x MODULE=FILE pass FILE's content as extra data to MODULE
-a, --timeout=SECONDS abort scanning after the given number of SECONDS
-k, --stack-size=SLOTS set maximum stack size (default=16384)
-r, --recursive recursively search directories
-f, --fast-scan fast matching mode
-w, --no-warnings disable warnings
-v, --version show version information
-h, --help show this help and exit
Send bug reports and suggestions to: vmalvarez@virustotal.com .- modules - like extensions to YARA’s core functionality;
- external variables;
- including files;
The base of the syntax of a YARA rule set is this:
rule RuleName
{
strings:
$test_string1= "Testing"
$test_string2= {C6 45 ?? ??}
condition:
$test_string1 or $test_string2
}all of them /* all strings in the rule */
any of them /* any string in the rule */
all of ($a*) /* all strings whose identifier starts by $a */
any of ($a,$b,$c) /* any of $a, $b or $c */
1 of ($*) /* same that "any of them" */rule RuleName
{
meta:
author = "Catalin George Festila - rule 001 "
description = "tell something to the computer"
strings:
$test_string1= "first step "
...
Posted by
Cătălin George Feștilă
 Labels:
2017,
Fedora,
Fedora 25,
linux,
linux tools,
security,
YARA
Labels:
2017,
Fedora,
Fedora 25,
linux,
linux tools,
security,
YARA
Saturday, April 15, 2017
The whiptail tool .
This command let you deal with many display dialog boxes from shell scripts.
The command is named whiptail and you can read and see simple examples with this command here.
Note: --infobox is almost useless in an xterm, because whiptail writes to the other screen xterm makes available but you can use the --msgbox
The tutorial of this day will show you how to put the text from a text file to the screen.
First, you need a text file with a size of your shell screen and this will be used by this command.
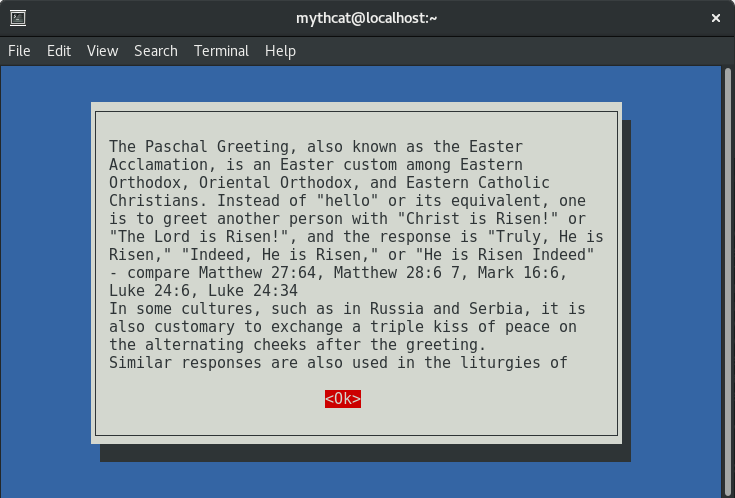
For example, I used this text from Wikipedia into my text file named greeting.txt, see content :
The Paschal Greeting, also known as the Easter Acclamation, is an Easter custom among Eastern Orthodox, Oriental Orthodox, and Eastern Catholic Christians. Instead of "hello" or its equivalent, one is to greet another person with "Christ is Risen!" or "The Lord is Risen!", and the response is "Truly, He is Risen," "Indeed, He is Risen," or "He is Risen Indeed" - compare Matthew 27:64, Matthew 28:6 7, Mark 16:6, Luke 24:6, Luke 24:34 In some cultures, such as in Russia and Serbia, it is also customary to exchange a triple kiss of peace on the alternating cheeks after the greeting. Similar responses are also used in the liturgies of other Christian churches, but not so much as general greetings.
To use the whiptail command just use this into your shell:
The command is named whiptail and you can read and see simple examples with this command here.
Note: --infobox is almost useless in an xterm, because whiptail writes to the other screen xterm makes available but you can use the --msgbox
The tutorial of this day will show you how to put the text from a text file to the screen.
First, you need a text file with a size of your shell screen and this will be used by this command.
For example, I used this text from Wikipedia into my text file named greeting.txt, see content :
The Paschal Greeting, also known as the Easter Acclamation, is an Easter custom among Eastern Orthodox, Oriental Orthodox, and Eastern Catholic Christians. Instead of "hello" or its equivalent, one is to greet another person with "Christ is Risen!" or "The Lord is Risen!", and the response is "Truly, He is Risen," "Indeed, He is Risen," or "He is Risen Indeed" - compare Matthew 27:64, Matthew 28:6 7, Mark 16:6, Luke 24:6, Luke 24:34 In some cultures, such as in Russia and Serbia, it is also customary to exchange a triple kiss of peace on the alternating cheeks after the greeting. Similar responses are also used in the liturgies of other Christian churches, but not so much as general greetings.
To use the whiptail command just use this into your shell:
[mythcat@localhost ~]$ whiptail --textbox /dev/stdin 19 59 <<<"$(cat greeting.txt)"
Posted by
Cătălin George Feștilă
 Labels:
2017,
Fedora,
Fedora 25,
linux,
linux tools,
tutorial,
tutorials,
whiptail
Labels:
2017,
Fedora,
Fedora 25,
linux,
linux tools,
tutorial,
tutorials,
whiptail
Linux: tools to scan a Linux server for malware and rootkits.
This tools are: chkrootkit, rkhunter, fuser and ISPProtect.
All of this tools can be install under Fedora 25 with dnf tool.
First tool is chkrootkit is a classic rootkit scanner.
It checks your server for suspicious rootkit processes and checks for a list of known rootkit files.
[root@localhost mythcat]# chkrootkit
ROOTDIR is `/'
Checking `amd'... not found
Checking `basename'... not infected
Checking `biff'... not found
Checking `chfn'... not infected
Checking `chsh'... not infected
Checking `cron'... not infected
Checking `crontab'... not infected
Checking `date'... not infected
Checking `du'... not infected
Checking `dirname'... not infected
Checking `echo'... not infected
...[root@localhost mythcat]# rkhunter --update
[ Rootkit Hunter version 1.4.2 ]
Checking rkhunter data files...
Checking file mirrors.dat [ No update ]
Checking file programs_bad.dat [ No update ]
Checking file backdoorports.dat [ No update ]
Checking file suspscan.dat [ No update ]
Checking file i18n/cn [ No update ]
Checking file i18n/de [ No update ]
Checking file i18n/en [ No update ]
Checking file i18n/tr [ No update ]
Checking file i18n/tr.utf8 [ No update ]
Checking file i18n/zh [ No update ]
Checking file i18n/zh.utf8 [ No update ]
[root@localhost mythcat]# rkhunter --propupd
[ Rootkit Hunter version 1.4.2 ]
File created: searched for 172 files, found 136
[root@localhost mythcat]# rkhunter -c --enable all --disable none
[ Rootkit Hunter version 1.4.2 ]
Checking system commands...
Performing 'strings' command checks
Checking 'strings' command [ OK ]
Performing 'shared libraries' checks
Checking for preloading variables [ None found ]
Checking for preloaded libraries [ None found ]
Checking LD_LIBRARY_PATH variable [ Not found ]
Performing file properties checks
Checking for prerequisites [ OK ]
/usr/bin/awk [ OK ]
/usr/bin/basename [ OK ]
/usr/bin/bash [ OK ]
/usr/bin/cat [ OK ]
/usr/bin/chattr [ OK ]
/usr/bin/chmod [ OK ]
/usr/bin/chown [ OK ]
/usr/bin/cp [ OK ]
...[root@localhost mythcat]# fuser -vn tcp 5222
...[root@localhost mythcat]# fuser -vn tcp 19635
...
Posted by
Cătălin George Feștilă
 Labels:
2017,
chkrootkit,
commands,
Fedora,
Fedora 25,
fuser,
ISPProtect,
linux,
linux tools,
rkhunter,
security,
tutorial,
tutorials,
vulnerability
Labels:
2017,
chkrootkit,
commands,
Fedora,
Fedora 25,
fuser,
ISPProtect,
linux,
linux tools,
rkhunter,
security,
tutorial,
tutorials,
vulnerability
Tuesday, March 28, 2017
The journalctl command.
This is a good Linux command for Linux maintenance.
The first step is to read the documentation:
This helps you with free space into your Linux OS.
For example, I got 3 Gigabytes of data in just 3 days.
retain only the past 500 MB
The first step is to read the documentation:
[root@localhost mythcat]# man journalctl
JOURNALCTL(1) journalctl JOURNALCTL(1)
NAME
journalctl - Query the systemd journal
SYNOPSIS
journalctl [OPTIONS...] [MATCHES...]
DESCRIPTION
journalctl may be used to query the contents of the systemd(1) journal
as written by systemd-journald.service(8).
If called without parameters, it will show the full contents of the
journal, starting with the oldest entry collected.
If one or more match arguments are passed, the output is filtered
accordingly. A match is in the format "FIELD=VALUE", e.g.
"_SYSTEMD_UNIT=httpd.service", referring to the components of a
structured journal entry. See systemd.journal-fields(7) for a list of
well-known fields. If multiple matches are specified matching different
fields, the log entries are filtered by both, i.e. the resulting output
will show only entries matching all the specified matches of this kind.
If two matches apply to the same field, then they are automatically
matched as alternatives, i.e. the resulting output will show entries
matching any of the specified matches for the same field. Finally, the
character "+" may appear as a separate word between other terms on the
command line. This causes all matches before and after to be combined
in a disjunction (i.e. logical OR).
...
This helps you with free space into your Linux OS.
For example, I got 3 Gigabytes of data in just 3 days.
# journalctl --vacuum-time=3d- by time
journalctl --vacuum-time=2djournalctl --vacuum-size=500M[root@localhost mythcat]# cat /etc/systemd/journald.conf[root@localhost mythcat]# systemctl status systemd-journald
● systemd-journald.service - Journal Service
Loaded: loaded (/usr/lib/systemd/system/systemd-journald.service; static; vendor preset: disabled)
Active: active (running) since Tue 2017-03-28 09:12:20 EEST; 1h 8min ago
Docs: man:systemd-journald.service(8)
man:journald.conf(5)
Main PID: 803 (systemd-journal)
Status: "Processing requests..."
Tasks: 1 (limit: 4915)
CGroup: /system.slice/systemd-journald.service
└─803 /usr/lib/systemd/systemd-journald
Mar 28 09:12:20 localhost.localdomain systemd-journald[803]: Runtime journal (/run/log/journal/) is 8.0M,
max 371.5M, 363.5M free.
Mar 28 09:12:20 localhost.localdomain systemd-journald[803]: Journal started
Mar 28 09:12:22 localhost.localdomain systemd-journald[803]: System journal (/var/log/journal/) is 3.9G,
max 4.0G, 23.8M free.
Mar 28 09:12:23 localhost.localdomain systemd-journald[803]: Time spent on flushing to /var is 915.454ms
Posted by
Cătălin George Feștilă
 Labels:
2017,
commands,
Fedora,
Fedora 25,
journalctl,
linux,
tutorial,
tutorials
Labels:
2017,
commands,
Fedora,
Fedora 25,
journalctl,
linux,
tutorial,
tutorials
Friday, March 17, 2017
Measure the charging with Ampere.
This android application let you to know more about your battery.
Just use it to measure the charging and discharging current of your battery.
-
Or, you can also use a hardware device and Fedora 25 to have a great life.
Just use it to measure the charging and discharging current of your battery.
-
Or, you can also use a hardware device and Fedora 25 to have a great life.
Wednesday, March 15, 2017
Fedora 25: First test with clamav antivirus.
This is a short tutorial about how to use ClamAV antivirus on Fedora 25.
First, you need to install it with this commands:
First, you need to install it with this commands:
[root@localhost mythcat]# dnf install clamav.x86_64
...
[root@localhost mythcat]# dnf install clamav-update.x86_64
...[root@localhost mythcat]# awk -F: '/^[^#]/ { print $1 }' /etc/freshclam.conf | uniq DatabaseDirectory /var/lib/clamav
UpdateLogFile /var/log/freshclam.log
LogFileMaxSize 2M
LogTime yes
LogVerbose yes
LogSyslog yes
LogFacility LOG_MAIL
LogRotate yes
DatabaseOwner clamupdate
DNSDatabaseInfo current.cvd.clamav.net
DatabaseMirror database.clamav.net
MaxAttempts 5
ScriptedUpdates yes
DetectionStatsCountry country-code
SafeBrowsing yes[root@localhost mythcat]# /usr/bin/freshclam
ClamAV update process started at Wed Mar 15 13:42:07 2017
main.cvd is up to date (version: 57, sigs: 4218790, f-level: 60, builder: amishhammer)
WARNING: getfile: daily-21724.cdiff not found on database.clamav.net (IP: 195.30.97.3)
WARNING: getpatch: Can't download daily-21724.cdiff from database.clamav.net
Trying host database.clamav.net (212.7.0.71)...
nonblock_connect: connect timing out (30 secs)
Can't connect to port 80 of host database.clamav.net (IP: 212.7.0.71)
WARNING: getpatch: Can't download daily-21724.cdiff from database.clamav.net
WARNING: getpatch: Can't download daily-21724.cdiff from database.clamav.net
WARNING: getpatch: Can't download daily-21724.cdiff from database.clamav.net
WARNING: getpatch: Can't download daily-21724.cdiff from database.clamav.net
WARNING: Incremental update failed, trying to download daily.cvd
Downloading daily.cvd [100%]
daily.cvd updated (version: 23205, sigs: 1789155, f-level: 63, builder: neo)
Downloading safebrowsing.cvd [100%]
safebrowsing.cvd updated (version: 45693, sigs: 2756150, f-level: 63, builder: google)
Downloading bytecode-279.cdiff [100%]
Downloading bytecode-280.cdiff [100%]
Downloading bytecode-281.cdiff [100%]
Downloading bytecode-282.cdiff [100%]
Downloading bytecode-283.cdiff [100%]
Downloading bytecode-284.cdiff [100%]
Downloading bytecode-285.cdiff [100%]
Downloading bytecode-286.cdiff [100%]
Downloading bytecode-287.cdiff [100%]
Downloading bytecode-288.cdiff [100%]
Downloading bytecode-289.cdiff [100%]
Downloading bytecode-290.cdiff [100%]
Downloading bytecode-291.cdiff [100%]
bytecode.cld updated (version: 291, sigs: 55, f-level: 63, builder: neo)
Database updated (8764150 signatures) from database.clamav.net (IP: 157.25.5.183)[root@localhost mythcat]# clamscan
/home/mythcat/.bash_logout: OK
/home/mythcat/.bash_profile: OK
...
----------- SCAN SUMMARY -----------
Known viruses: 8758441
Engine version: 0.99.2
Scanned directories: 1
Scanned files: 54
Infected files: 0
Data scanned: 71.80 MB
Data read: 189.96 MB (ratio 0.38:1)
Time: 13.968 sec (0 m 13 s)clamscan -r --bell -i / clamscan -r /home LibClamAV Warning: fmap_readpage: pread fail: ... --exclude-dir="^/sys"--exclude-dir=^/sys --exclude-dir=^/dev --exclude-dir=^/proc /home/mythcat/devil-linux-1.8.0-rc2-x86_64/install-on-usb.exe: Win.Trojan.Delfiles-17 FOUND
----------- SCAN SUMMARY -----------
Known viruses: 9042471
Engine version: 0.99.2
Scanned directories: 98653
Scanned files: 570740
Infected files: 1
Data scanned: 29750.14 MB
Data read: 48591.70 MB (ratio 0.61:1)
Time: 3819.053 sec (63 m 39 s)
Posted by
Cătălin George Feștilă
 Labels:
2017,
antivirus,
clamav,
Fedora,
Fedora 25,
linux,
linux tools,
tutorial,
tutorials
Labels:
2017,
antivirus,
clamav,
Fedora,
Fedora 25,
linux,
linux tools,
tutorial,
tutorials
Subscribe to:
Comments (Atom)

